In today’s tech-driven landscape, it’s hardly surprising that hackers are setting their sights on these devices. What’s even more concerning is the reality: a recent study discovered that over 1 in 5 Android phones have already been compromised.
These numbers hit close to home, emphasizing the critical importance of fortifying our digital security measures to protect our cherished devices and personal information. In this guide, we’ll explore the best ways to identify your Android phone is hacked or not.
Outline
ToggleWhat is Phone Hacking?
Phone hacking is when someone gets into your smartphone without permission. Hackers do this to take your personal info, put harmful stuff on your phone, or control it from far away. They might steal your money info, private chats, and more. They can even put bad software, called malware, on your phone to cause problems. This is a big violation of your privacy and can harm you in many ways.
Signs Your Android Phone is Hacked
1. Data Usage is Higher Than Normal
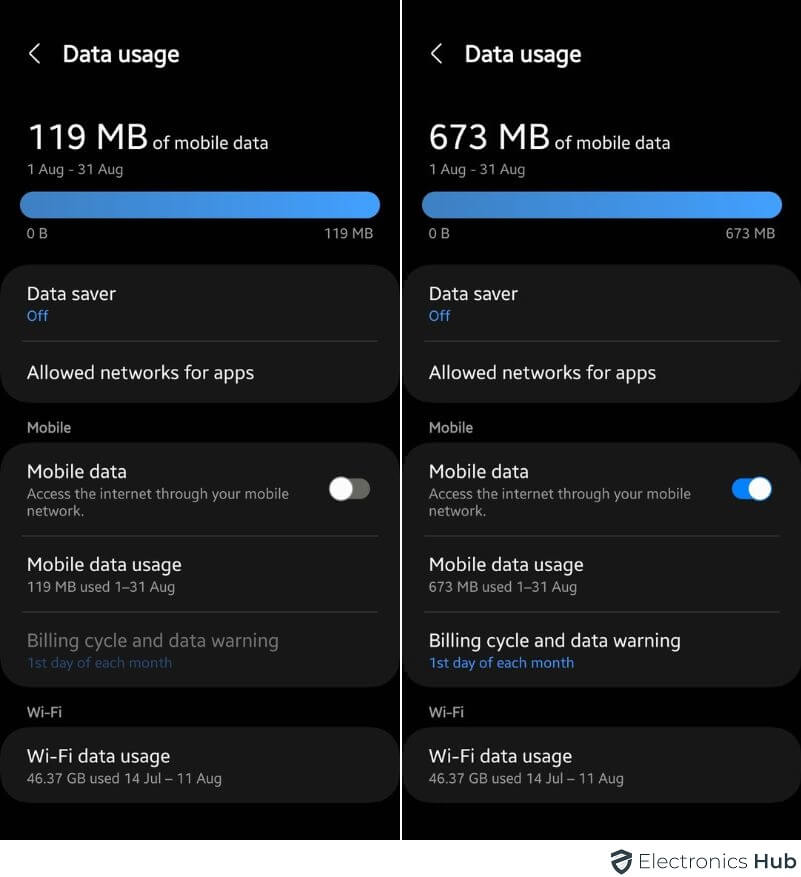
Hackers can turn your phone into a tool for “mining” cryptocurrency. This process uses a lot of your phone’s power, drawing it from your data plan. So, if your phone is hacked, you might see your data usage going crazy because of these sneaky activities.
2. Strange or Inappropriate Pop Ups
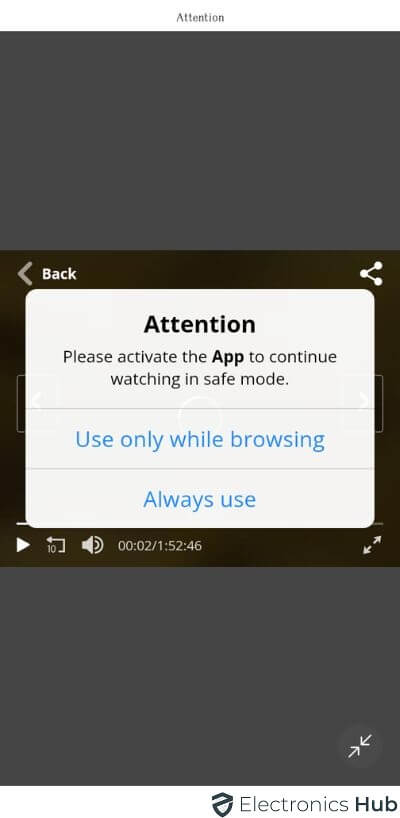
These pop-ups can take various forms:
- Warnings claiming your phone has malware.
- Offers to fix your phone for a fee.
- Displays of explicit or offensive content.
- Requests for personal info like credit card or Social Security numbers.
If you encounter such pop-ups, it’s crucial not to click them. Instead, take these steps:
- Close the pop-up.
- Use a trusted antivirus or anti-malware app to scan your phone.
- Update your passwords for all online accounts.
3. Phone is Too Hot
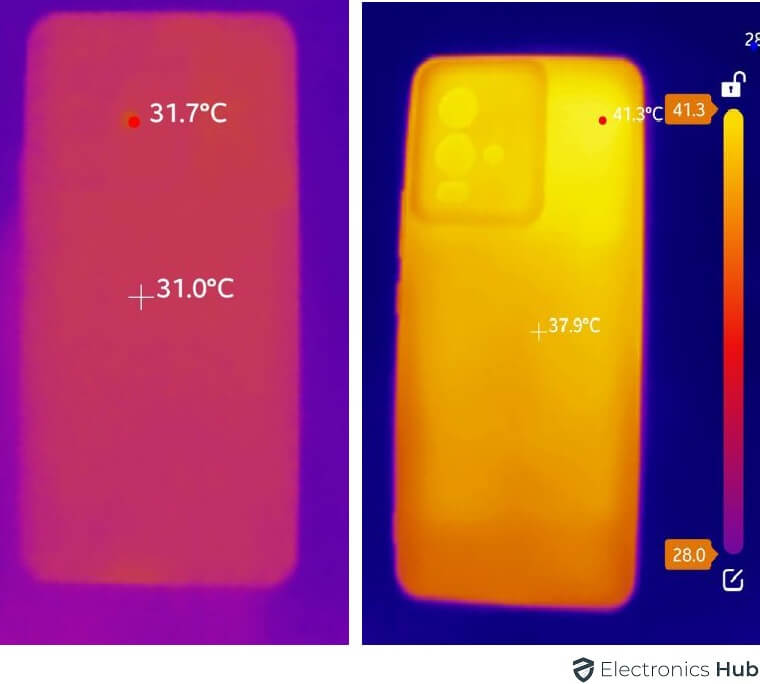
When your phone’s temperature rises beyond the norm, it’s worth considering:
- The possibility of malware presence.
- Background activities by malicious software.
- The hacker’s attempt to exploit your device.
To respond:
- Monitor your phone’s temperature.
- Run a thorough scan using reputable antivirus or anti-malware tools.
- If necessary, take action to remove the malware and reinforce your phone’s security against potential breaches.
4. Texts or Calls That Are Not Made By You
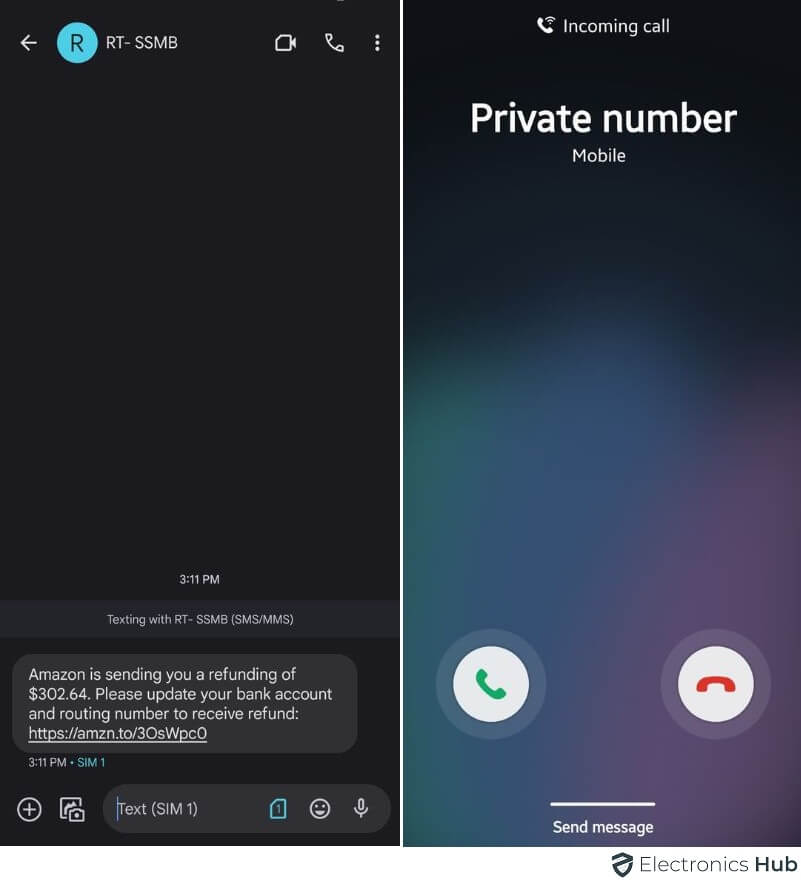
Signs of potential hacking linked to calls or texts:
- Strange numbers showing up in your call log.
- Receiving texts from unfamiliar numbers.
- Noticing odd actions in your online accounts, like unauthorized logins or password changes.
If hacking seems likely, secure your device by:
- Checking for threats using a trusted antivirus or anti-malware app.
- Changing passwords for all your online accounts.
5. Phone is Performing Slowly

6. Battery is Draining Faster

7. Service Disruptions
8. Unexpected Bill Charges
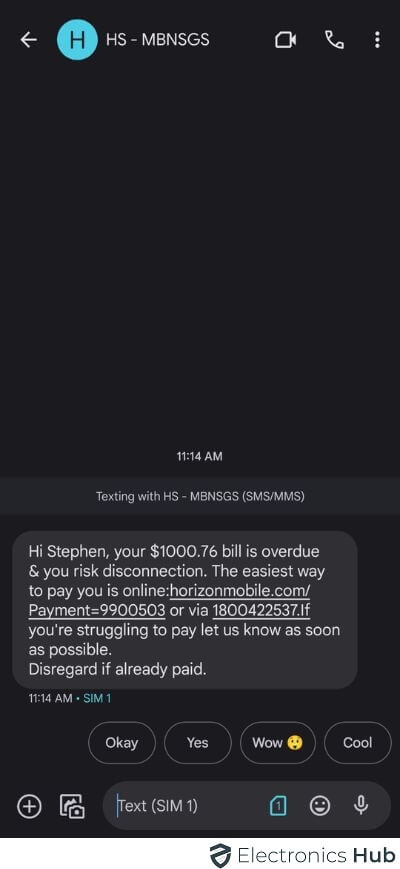
Check by Dialing these numbers to see your phone is hacked.
What to do When Your Phone is Hacked?
1. Delete Suspicious Apps
- Ensure app permissions: Before removing an app, review its permissions. If unnecessary access is granted, revoke it.
- Watch for odd behaviour: If apps open autonomously or battery drains swiftly, a suspicious app could be the cause. Scan for malware and delete doubtful apps.
- Download cautiously: Stick to trusted sources like Google Play Store or Apple App Store. Make clear of third-party sites.
2. Run Anti Malware Software
Safeguarding your phone against malware is paramount. Malicious software can infiltrate via deceitful links, infected attachments. Once inside, it can plunder your private data—passwords, credit card info, contacts—while also exploiting your device for spam and attacks. Counter this threat by using anti-malware software.
3. Reset Phone

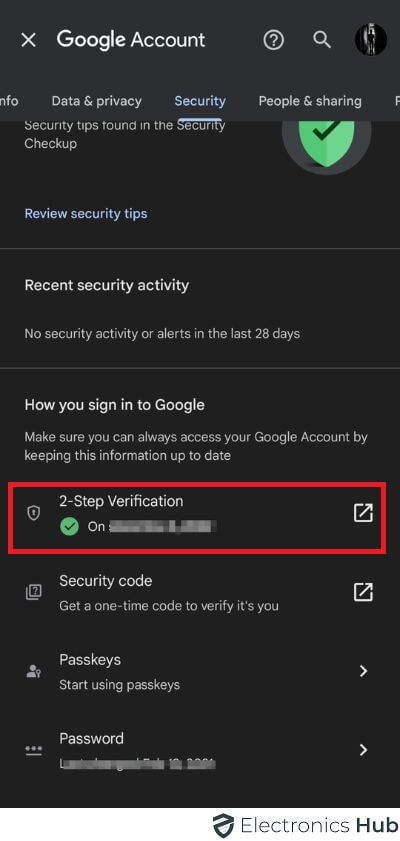
4. Change Passwords and Enable 2FA
5. Inform Your Contacts
Alert your contacts about the phone hack to prevent them from falling victim to suspicious messages or calls. Hackers might exploit your phone to send scams or emails to your contacts. By notifying them via text, email, or social media, you can inform them to recognize potential risks.
6. Contact Service Provider
7. Disconnect Your Phone From Internet
8. Set Password Manager
Elevate your security with a password manager—a tool that stores and organizes your passwords. In the wake of a phone hack, it becomes an essential shield, helping you manage passwords and thwart hackers’ access to your accounts.
How Phones get Hacked?
Phones can be hacked through various methods, and it’s essential to be aware of these potential vulnerabilities to better protect your device. Here are some common ways phones can be hacked:
- Malicious Apps: Downloading and installing apps from untrusted sources can expose your phone to malware and other malicious software. These apps may compromise your device’s security and grant unauthorized access to your data.
- Phishing Attacks: Cybercriminals often use phishing techniques to trick users into revealing sensitive information, such as passwords or credit card details. This can occur through deceptive emails, text messages, or fake websites that appear legitimate.
- Insecure Wi-Fi Networks: Connecting to unsecured or public Wi-Fi networks can expose your phone to potential hacking. Hackers may exploit vulnerabilities in the network to intercept your data or launch attacks on your device.
- Outdated Software: Using outdated operating systems or applications can leave your phone vulnerable to security flaws. Hackers often target devices with known vulnerabilities that have not been patched through software updates.
- SMS Phishing (Smishing): Similar to email phishing, smishing involves fraudulent messages sent via SMS. These messages may contain malicious links or prompt users to provide sensitive information.
- Bluetooth Exploits: Bluetooth vulnerabilities can be exploited by hackers to gain unauthorized access to your phone. It’s crucial to keep Bluetooth disabled when not in use and to use secure connections when pairing devices.
- Weak Passwords: Using weak or easily guessable passwords makes it easier for hackers to gain access to your accounts and personal information. Strong, unique passwords and two-factor authentication can enhance security.
- Social Engineering: Hackers may use social engineering techniques to manipulate individuals into divulging confidential information. This can involve impersonating trusted entities or using psychological tactics to exploit human behavior.
- Spyware and Malicious Software: Malicious software, such as spyware or keyloggers, can be installed on a device without the user’s knowledge. These programs can record keystrokes, capture screen activity, and collect sensitive information.
- Network Spoofing: Attackers can set up fake Wi-Fi networks or cell towers to trick devices into connecting to them. Once connected, the hacker can intercept and manipulate data transmitted between the device and the internet.
To minimize the risk of hacking, it’s important to stay vigilant, use reputable app stores, keep software up to date, avoid connecting to insecure networks, and be cautious of unsolicited messages or requests for sensitive information.
Possible Dangers to Your Hacked Android Phone
1. False Advertisements
“Stay cautious of hackers’ deceptive ads manipulate as genuine offers. These ads promise freebies, discounts, and more. However, clicking them can lead to malicious websites that plant malware on your phone.
2. Malware
Malware, harmful software, poses threats to your phone’s security. It sneaks in through malicious links, infected attachments, or fake apps. Once infiltrated, it can swipe sensitive info—passwords, credit card data, contacts—and misuse your phone for spam or attacks.
3. Public Wi-Fi

Best Ways to Protect Your Phone From Hackers
- Turn off the Bluetooth when not in use
- Don’t save information like passwords or credit card information on your phone
- Regularly monitor your phone to find out unusual activity
- Update your software and operating system
- Create a unique password for your phone
- Use a password lock for sensitive apps
Conclusion
In a digitally connected world, vigilance is key. A staggering 76% of hacking cases involve suspicious apps, while 64% lead to surprise bill spikes. 68% of hacks cause service disruptions. Prioritize strong, unique passwords and activate two-factor authentication (2FA). Swift action is crucial – 47% of victims face financial loss due to unexplained charges. Public Wi-Fi? Risky. Hackers exploit it to intercept data. Remember, your phone can be an unwitting accomplice in cybercrimes. Safeguard it against malware, be cautious with apps, and maintain a watchful eye for unusual behaviour. Your proactive efforts ensure your phone stays secure
Phone Hacked – FAQs
Ans: Certo Mobile Security finds a threat on your device
This free app will allow you to scan your device and find out for sure if there is malicious software installed on your Android system.
Ans: If you want to stop phone tracking, you can change your phone settings, switch to a private browser, configure your app permissions more carefully, or use a VPN.
Ans: Yes, a factory reset can remove most malware and return your phone to its original state. However, some advanced malware can persist even after a factory reset, so combining it with other security measures is recommended.
Ans: Public Wi-Fi networks can be risky as they are more susceptible to hacking. Avoid accessing sensitive information on public Wi-Fi, and consider using a virtual private network (VPN) for added security.
Ans: Phishing attempts often involve unsolicited emails or messages asking for personal information, passwords, or payment details. Be cautious of misspellings, generic greetings, and urgent requests.